Phase - Configuration
First phase of using PETEP in penetration testing is configuration phase.
Create Project
If you want to start testing an application, you have to create your own project first. Just open PETEP and click on "New" button.
When setting up the project, I recommend using one of PETEP presets (preferably FULL), because then you do not have to configure modules manually.

Configure Proxies
In order to test applications, you have to setup proxies for them. Usually you can find out domain, which is used by the tested application for connecting to the server. After that you can edit /etc/hosts file to translate the domain to 127.0.0.1 and configure PETEP proxy targeting the real server.
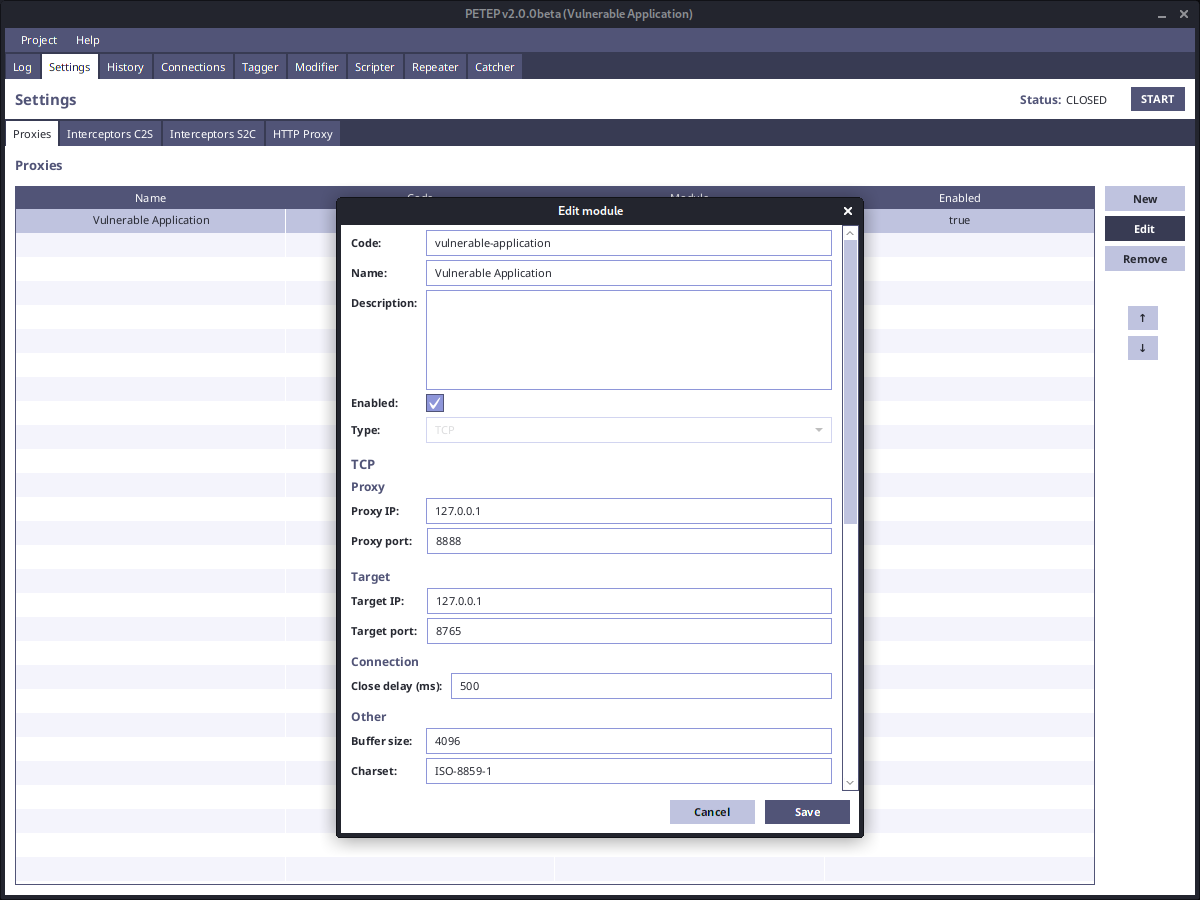
In the example above, the target server is running on 127.0.0.1:8765 and the PETEP proxy is running on 127.0.0.1:8888.
If the target application cannot be forced to communicate with a proxy, you can try to use Deluder, which allows you to hook the target process and intercept networking/encryption library functions.
Configure Interceptors
Interceptors represent modules like Tagger, Modifier and many others. (These modules are described in User Guide.) For easy usage, I recommend using the FULL preset and then optionally configuring the interceptor modules.
Important thing to know is that the order of interceptors matters. So, for example, if you want to automatically modify data after you edit them in Catcher, you have to have Modifier after Catcher interceptor. (This is especially important when using Modifier/Scripter for automatic repairing of PDUs - like length fixing, ...)