Buffer Over-read Testing
Buffer related vulnerabilities like buffer overflow and buffer over-read allow attacker to manipulate program memory (read/write from/into it). In PETEP, we can test buffer vulnerabilities using Repeater (preferably), Catcher or Modifier.
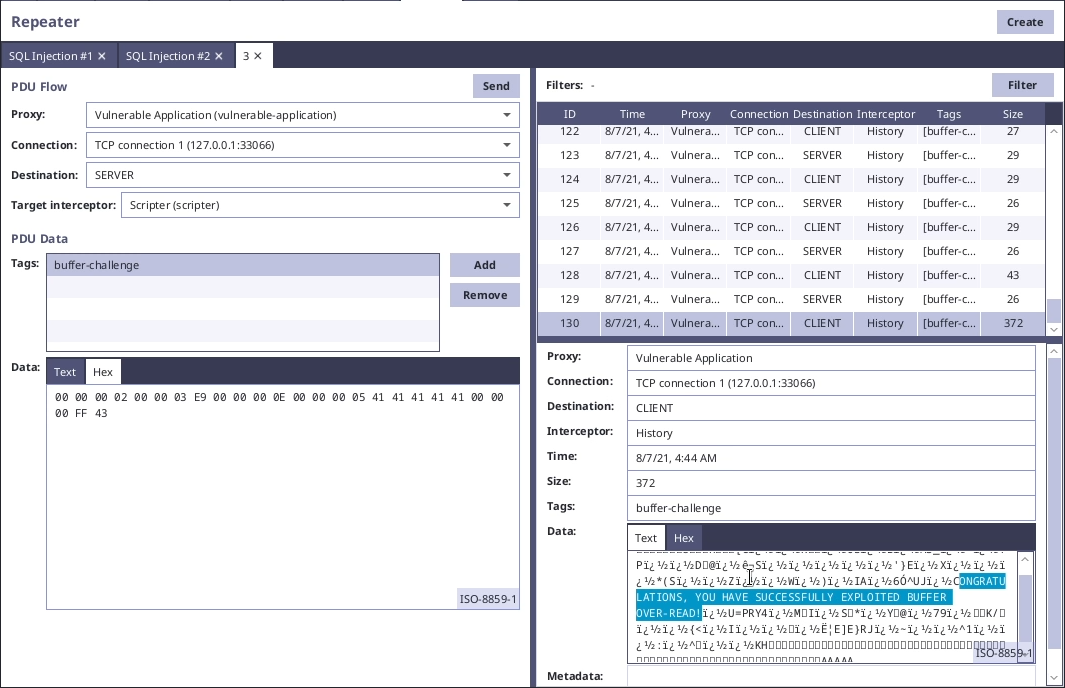
In our example vulnerable application, there is buffer over-read challenge, which simulates buffer over-read vulnerability in protocol parsing. There is a list of items being sent to the server, which contains the following bytes:
00 00 00 02 00 00 03 E9 00 00 00 1E 00 00 00 06 49 74 65 6D 20 31 00 00 00 06 49 74 65 6D 20 32 00 00 00 06 49 74 65 6D 20 33If we analyse the PDU, we can see that after the first 12 header bytes (4B type, 4B target, 4B length) there are length bytes for each item in the list followed by the item value. For example "Item 1" is represented by length bytes "00 00 00 06" and item value "49 74 65 6D 20 31".
After playing with these length bytes, we will find out that it is possible to let the application over-read the buffer, because the deserializer will read more bytes than the PDU contains. We can achieve this by changing the length bytes of the last item to "00 00 00 FF".