Phase - Assessment & Exploitation
After you have understood the structure of communication and prepared scripts/extensions to help you work with it, you can start with assessment phase. During assessment and exploitation, all modules are often used (Tagger, Modifier, Repeater, Catcher, Scripter, ...), and the phase is usually the longest.
There are several ways to approach assessment. One of the greatest factors is whether the application allows repetition of PDUs. If the repetition is allowed, Repeater module is prefered, but if the repetition is not allowed, users have to work with Catcher and Modifier to find vulnerabilities.
Assessment - With Repeating Allowed
If repeating of PDUs is allowed, penetration testing will be probably easier. You can easily send interesting PDUs to Repeater from History extension:
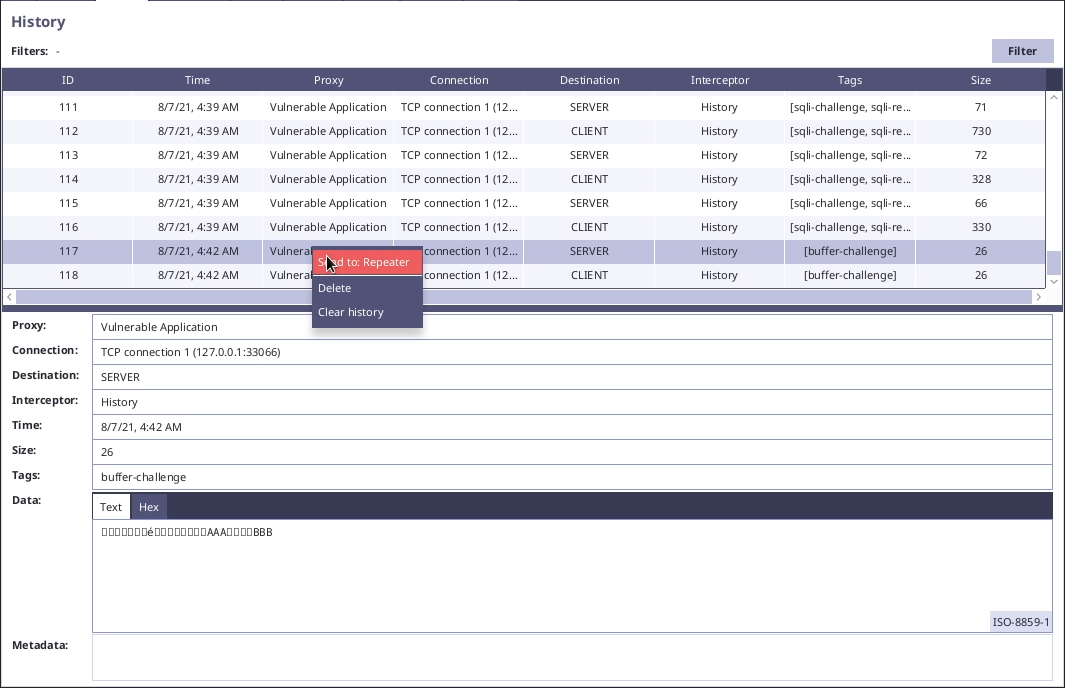
In repeater you can try to perform various modifications to discover vulnerabilities. (See the links under "Penetration Testing" menu for concrete vulnerability examples.)

When using Repeater, change the target interceptors, so that the PDUs go through all processing you need.
Assessment - With Repeating Disallowed
If repeating of PDUs is not allowed, you have to use Catcher for finding vulnerabilities. For automatic exploitation of discovered vulnerabilities, you can use Modifier or Scripter for automatic PDU manipulation.
For example, in the vulnerable application we can find PDUs with data informing our client application about our role and name. We can discover the ability to switch the UI to admin mode by changing the role "00 00 00 01" to "00 00 00 05" in Catcher:
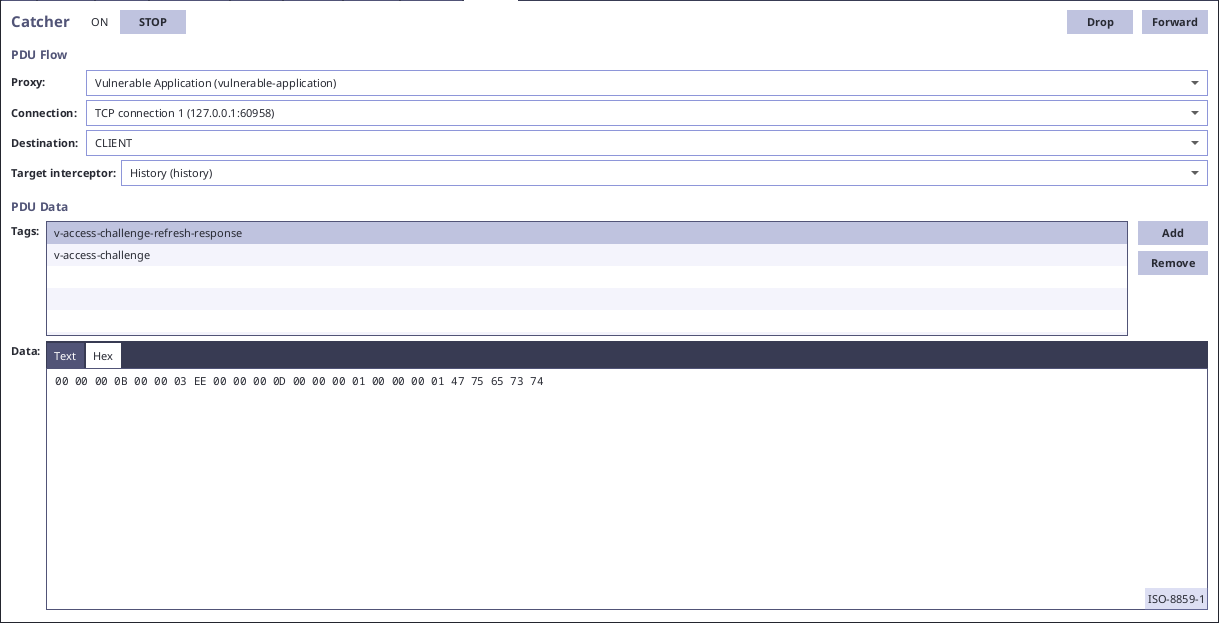
Automatic exploitation can be easily done by replacement of adequate bytes in specific PDUs:

Notice that the modifier rule enlarges the PDU by the replacement operation. This can be done, because we have created script for automatic length fixing. (Without the script it would not work and we would have to keep the same lengths of "what" and "with".)