Enumeration Testing
Enumeration vulnerability is often related to user enumeration, which allows attacker so enumerate user names or even user passwords. It is caused by different error messages for wrong user name and wrong password.
In our example vulnerable application, there is login simulation, which is vulnerable to enumeration. We can see that there are two different error messages:
Entered credentials (wrong username):
adminstrator:randompassword
Server response:
00 00 00 06 00 00 03 EB 00 00 00 04 00 00 00 02
Entered credentials (wrong password):
admin:randompassword
Server response:
00 00 00 06 00 00 03 EB 00 00 00 04 00 00 00 03From the payload content we can see that 0x00000002 signalizes wrong user name and 0x00000003 signalizes wrong password.
Since execution of enumeration attack manually would be almost impossible and endless task, we have to use External HTTP Proxy module for cooperation with third-party proxy tools, which have support for fuzzing. In our example we will setup Burp Suite with PETEP, send login request PDU to Intruder and configure it to use Simple list with top user names from dictionary.

To make the attack easier for us, we can create tagger rule for tagging data with "enum-interesting" tag, so that we are able to filter for all requests and only "success" responses. (By that we will be able to find valid user name requests in the history.) We will add the "enum-interesting" tag for all PDUs, which have tag "enum-login-request" or start with "00 00 00 06 00 00 03 EB 00 00 00 04 00 00 00 03" (wrong password).
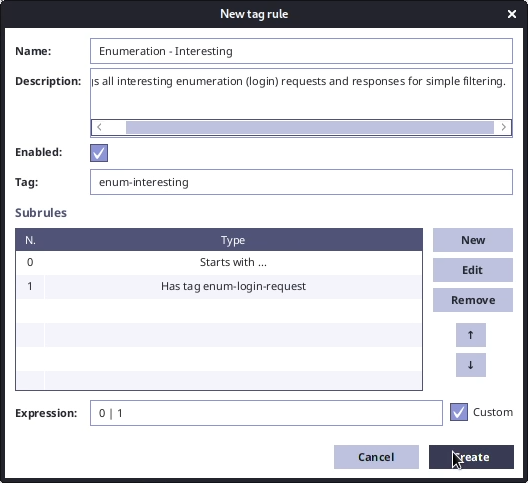
Now we can run the configured Intruder and after finishing the fuzzying we can filter for "enum-interesting" tag in History module.
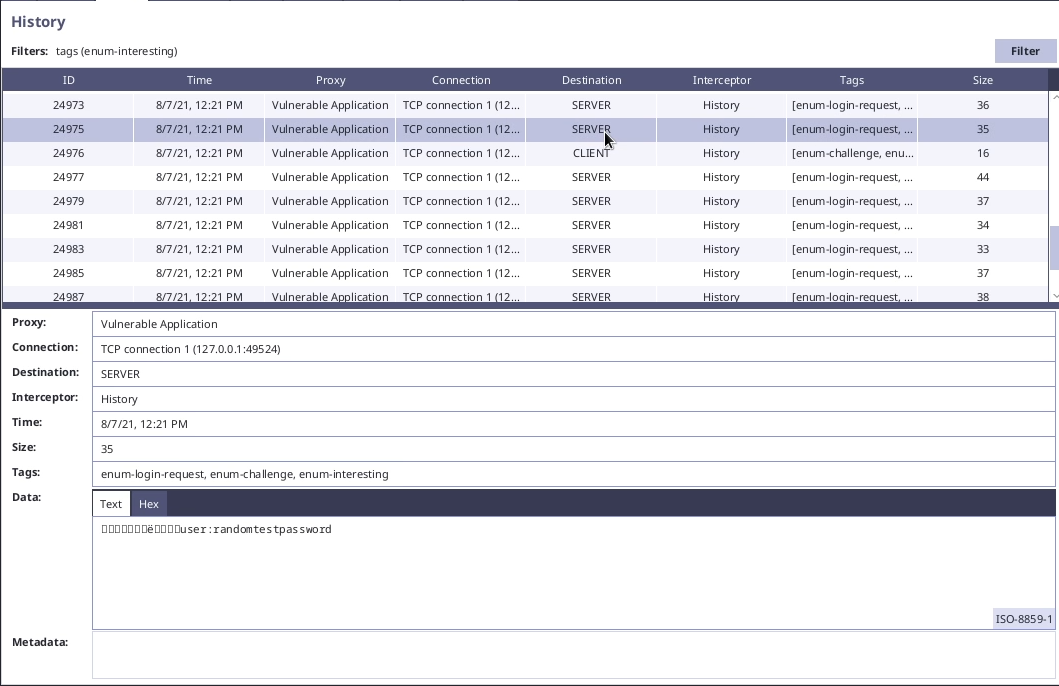
By this approach we can obtain user names and then we can do the same processes for enumerating user passwords.