Horizontal Access Control Testing
Horizontal Access Controls restrict access to various resources for different users. For example user 1 can access his resources, but not resources of user 2. Testing of horizontal access controls is usually done by tampering of various identifiers in PDUs. (For testing of horizontal access controls in PETEP we usually use Repeater and Catcher modules. For automatic fuzzying we can use External HTTP Proxy module and use external tools like Zap or Burp Suite.)
In our example vulnerable application, there is simulated functionality for obtaining user documents. On the following screen we can see the communication request and response for our document:
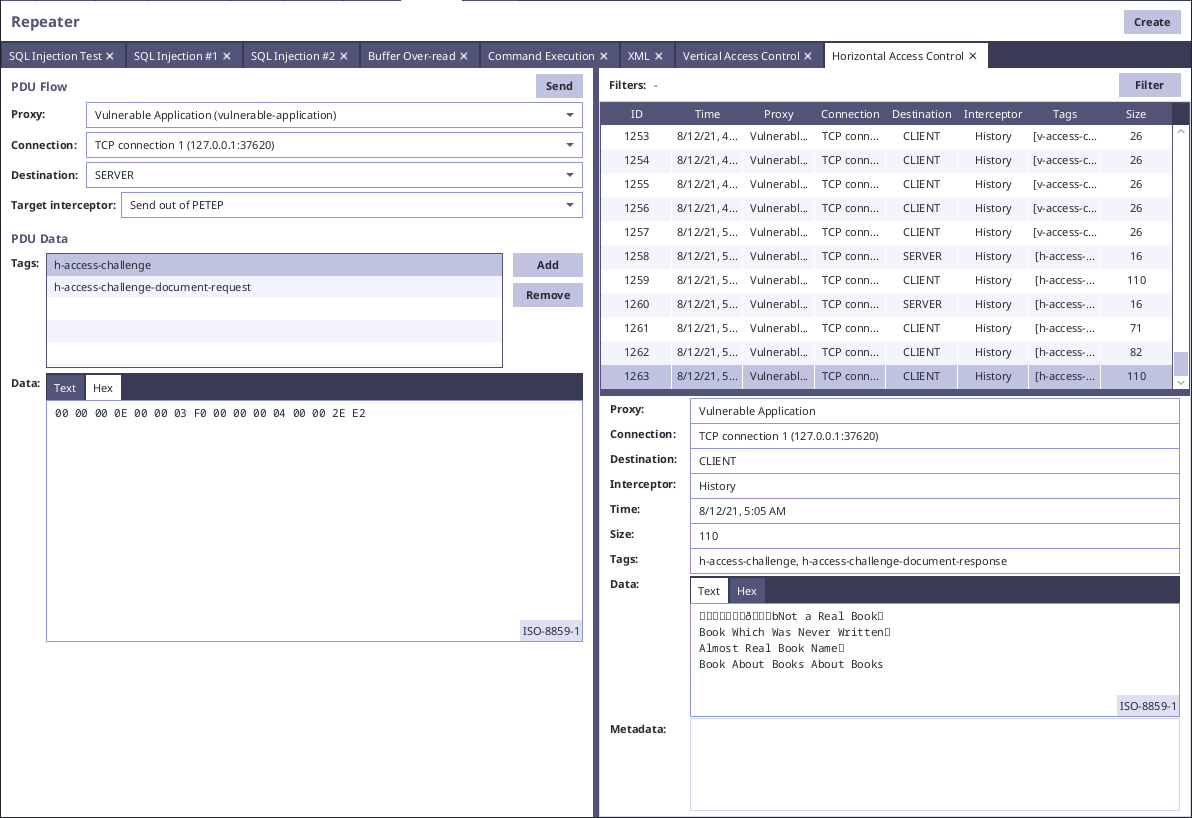
It is obvious from the payload data "00 00 2E E2" that it contains some kind of identifier of the document. We can change the bytes manually and see that there is error notifying us about nonexistence of the file:
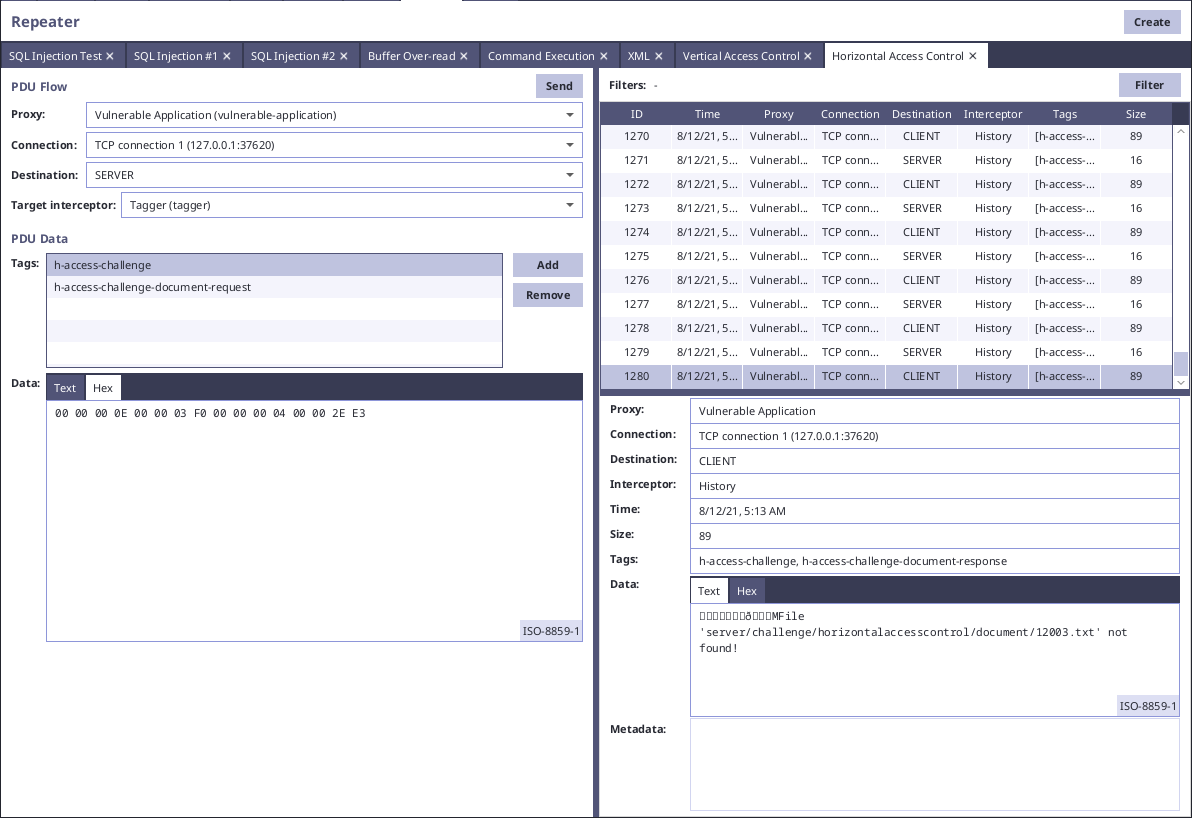
It shows us that the server probably does not have correct horizontal access controls in place and does not check if user has permissions for given document. If we want to find all documents on the server, we have to use some third-party tool for automatic fuzzying. In this case, we will setup PETEP to use ZAProxy using External HTTP Proxy module and in Zaproxy, we will see requests with serialized PDUs.
In the Zaproxy history we will find PDU for requesting the document and we will send it to Fuzzer and choose last 4 bytes as fuzz location. As payloads we have to use various bytes, so it is easier to generate these bytes in base64 encoding and load them in Zaproxy as a file with base64-decode processing. For generation, we will use Python:
import base64
START = 0
END = 20000
with open("payloads.txt", "w") as file:
for i in range(START, END + 1):
byte = (i).to_bytes(4, byteorder='big')
file.write(base64.b64encode(byte).decode('ascii'))
file.write('\n')This script will generate payloads in the following format:
AAAAAA==
AAAAAQ==
AAAAAg==
AAAAAw==
AAAABA==
AAAABQ==
...We will add this file to the Fuzzer payloads and add base64-decode processor with ISO-8859-1 encoding. Then we can configure the fuzzer to run at wanted pace and start the fuzzying.
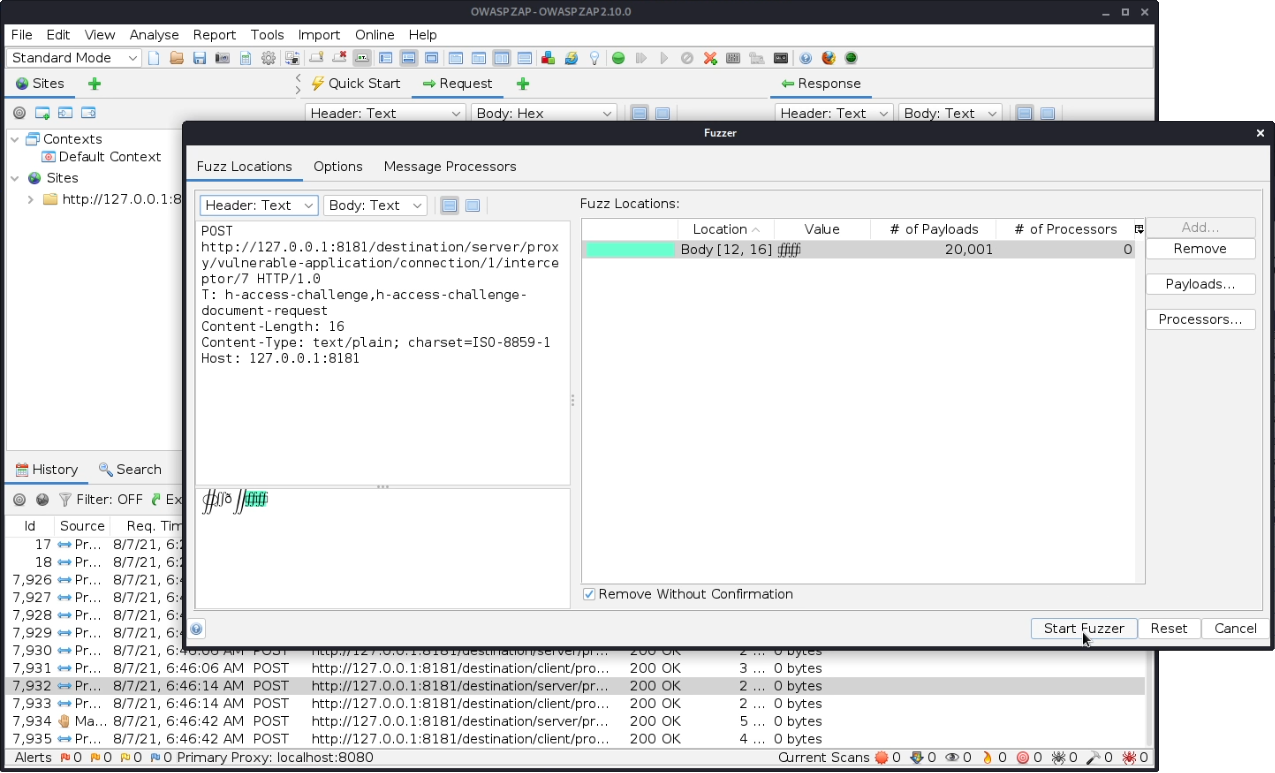
After the fuzzying finishes, we can go to PETEP history and filter for PDUs with horizontal access challenge tag and data, which do not contain ".txt' not found!". We are going to see the discovered documents.
